October 21, 2021
VPN Protocols: A Complete Guide for 2024
The average VPN has at least a couple of VPN protocols on offer, but what’s the difference [...]

WHAT’S IN THIS REVIEW?
Disclaimer: Partnerships & affiliate links help us create better content. Learn how.
A VPN protocol is used to create and manage an encrypted tunnel for user data, with popular options including OpenVPN, IKEv2, L2TP, and SSTP.
WireGuard has been described as the future of VPN protocols, and for good reason. It’s notably faster than the competition, and the code is powerful and lightweight. On the surface, it appears to be the perfect package.
However, WireGuard doesn’t dynamically assign the user with an IP address by default, so you’ll be using the same one each time. This is a serious privacy concern, which is why a number of VPN providers have taken steps to implement workarounds when offering the protocol to users.
In this guide, we cover the concerns with WireGuard IP connections and what CyberGhost, IVPN, and Mullvad offer to get around this issue.
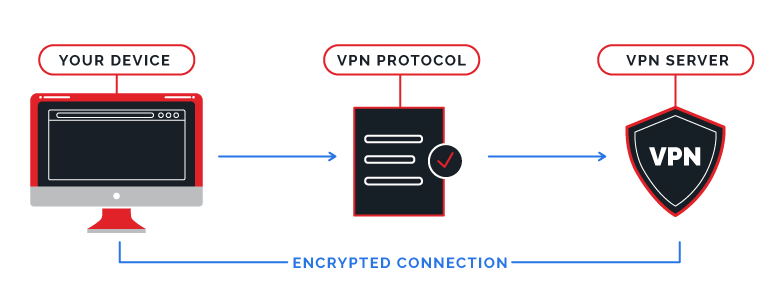
Let’s start with the basics. A VPN protocol is a set of instructions for transmitting your online traffic safely, often while assigning the user with a new IP address.
There are many protocols that have been released over the years, from famous open-source options to proprietary tech built for a specific service. They all have different pros and cons, and you can find out more about each one by checking out our Complete Guide to VPN protocols.
OpenVPN and L2TP are two examples of protocols used frequently by commercial VPN services, but we’re focusing on WireGuard specifically and its issues relating to privacy.
Created by Edge Security cryptographer, Jason A. Donenfeld, WireGuard’s first stable release, or version 1.0.0., was on March 29, 2020. The main aim of WireGuard is to simplify the encryption process thanks to less code and a cleaner design. This means that it’s a viable option in terms of security and can be audited easily.
One of the best things about WireGuard is its simplicity. At just 4,000 lines of code, it’s dwarfed by the likes of OpenVPN (70,000 code lines), offering a streamlined solution that also happens to be open-source.
“Because throttling OpenVPN connections is now the norm for restrictive networks, WireGuard comes as a breath of fresh air.”
CyberGhost
The smaller codebase should help to improve security, with less scope for problems that go under the radar for any significant period of time. It’s also a speedy solution, so it’s recommended for anything from gaming to downloading large files.
If WireGuard is available, I always use it to conduct speed tests during VPN reviews for this reason. For example, I ran a quick speed test just now, getting roughly 375 Mbps without a VPN connection. While using Surfshark and the WireGuard protocol, the results are as follows:
250 Mbps isn’t bad at all, but what if the protocol is switched to the tried-and-tested IKEv2 instead of WireGuard? The connection speed slowed to roughly 190 Mbps or about half of the original number achieved during testing.
Results are likely to be similar no matter which VPN provider you’ve signed up with. WireGuard is undeniably fast.
If you’re wary of commercial VPNs, as you probably should be, the protocol is a solution that ticks many of the boxes despite the lack of an audit at the current time of writing. OpenVPN is still seen as the safer option, but that could all change depending on how WireGuard is developed in the future as it begins to be used more widely by commercial providers.
The protocol isn’t without its share of issues if online privacy is your main aim. A number of VPNs have yet to offer WireGuard support due to security concerns, as well as the work it takes to implement it properly.
A common concern is how WireGuard works to assign the user with an IP address. It uses a static IP instead of using a different one each time like OpenVPN or IKEv2. (This makes it faster, but much less secure.)
Theoretically, it means that a VPN server has to keep logs of user data, including your real IP and connection timestamps. A number of VPN providers have worked to solve this issue, which we’ll get into below.
Rather than being a “flaw,” this is an intentional design of the protocol. WireGuard is speedy and offers great security, but that comes at a cost in terms of privacy.
Of course, you’re always going to have to trust that a VPN will get rid of user data, including connection logs and the sites you’ve visited while signed into their service. Regardless, it’s easy to see why some providers have stuck with OpenVPN for now.
It’s also not the greatest when it comes to bypassing firewalls. If the network admin blocks all UDP ports, they’ll block all WireGuard traffic since it only runs over UDP, and it can’t use TCP.
A variety of commercial VPNs have taken steps to ensure that users will be safe and secure while using their services in combination with WireGuard. We’ve listed some of the best VPNs to use with WireGuard below, offering a mix of solutions to the IP issues.
CyberGhost offers WireGuard with multiple apps and devices, and they even made a donation to Wireguard development in 2021.
They say: “OpenVPN has become the standard protocol for security and privacy. Sadly, it’s now also a target for anti-VPN systems… Because throttling OpenVPN connections is now the norm for restrictive networks, WireGuard comes as a breath of fresh air.”
They offer over 6,400 high-speed servers in a range of locations dotted around the globe, making it a great choice if you’re looking for a WireGuard-friendly provider.
IVPN was one of the first providers to implement the WireGuard protocol, although they’re quick to admit that it took significant work to get it right:
“WireGuard was not designed with privacy VPN providers in mind. In addition, it leaves certain aspects (e.g. IP address assignment, key distribution, etc.) to the responsibility of the implementer. As a result, some privacy issues exist which all responsible VPN providers must resolve. These issues do not in any way represent a weakness of the WireGuard protocol itself, they are simply aspects which the protocol designers intentionally left out.”
It’s nothing that we haven’t mentioned above, but it’s good that they recognize the potential issues that could arise while using the protocol.
In line with their transparent approach, Mullvad goes into detail when discussing the internal WireGuard IP being a static address, mentioning a number of potential issues:
“We acknowledge that keeping a static IP for each device, even internally, is not ideal. Why? Because if a user experiences WebRTC leaks, that static internal IP address could leak externally. As another example, applications running on your device can find out your internal IP, and if you’ve installed software that is malicious, it can also leak that information.”
They go on to say: “And theoretically, a static internal IP that is leaked, together with obtaining a payment record, could help to identify a user. Having said that, we still believe that WireGuard overall is in a better state than OpenVPN.”
Additionally, the Mullvad app automatically replaces WireGuard keys once per week, but the user will also be able to do so manually. The path is as follows:
Gear Icon > Advanced > WireGuard Key, then click on Regenerate Key
This can be done as many times as you like, although an automated system would arguably be better.
Mullvad also notes that they’re taking part in the development of WG-dynamic. It should offer “the ability to dynamically assign a new internal IP every time a connection is made,” removing much of the hassle from the process in the future.
Recently, bigger providers like NordVPN and ExpressVPN have released their own proprietary VPN protocols to solve the privacy issues seen with WireGuard.
Rather than using WireGuard directly, NordVPN has opted for a proprietary solution in the form of NordLynx. They also highlight the privacy issues seen with the use of a static internal IP address:
“WireGuard alone can’t ensure complete privacy. It can’t dynamically assign IP addresses to everyone connected to a server. Therefore, the server must contain a local static IP table to know where internet packets are traveling from and to whom they should return. It means that the user’s identity must be stored on the server and linked to an internal IP address assigned by the VPN.”
In response to these issues, they have developed a double NAT (Network Address Translation) system. It creates two local network interfaces for each user. The first assigns a local IP address to all users connected to a server. Unlike the original WireGuard protocol, each user gets the same IP address to enhance anonymity.
As NordVPN explains it: “Once a VPN tunnel is established, the second network interface with a dynamic NAT system kicks in. The system assigns a unique IP address for each tunnel. This way, internet packets can travel between the user and their desired destination without getting mixed up.”
This means that there is no identifiable user data stored on their servers.
ExpressVPN is another example of a larger commercial provider that uses a proprietary protocol (Lightway) instead of WireGuard.
Released in the summer of 2021, Lightway is a very new VPN protocol released by ExpressVPN users report delivers fast connections. It’s also ExpressVPN’s way of avoid issues related to a static IP address.
WireGuard is clearly the winner if speed is your main priority, although VPN providers will have to use their own solutions to ensure anonymity in the meantime while the protocol is in use.
Proprietary methods like NordLynx are also a viable solution, as well as upcoming features such as WG-dynamic.
This doesn’t mean that WireGuard isn’t as important as it’s made out to be, and it’s worth taking into account that the stable 1.0 Linux release only went live in 2020. Time is still on their side, and it’s seen as an experimental option whose best is yet to come.
It’s worth being aware of the various security risks associated with WireGuard, which isn’t a magical invention that is going to solve all issues relating to VPN protocols. Instead, it comes with its own range of pros and cons, and they should be weighed up accordingly each time before you use it to go online.
It’s easy to see why a number of providers have yet to offer WireGuard support, especially when the main benefit seems to be improved speeds at the potential expense of anonymity.
Even so, the boost in performance is viable enough to make larger VPN providers take notice, with many offering workarounds so their users can get the best of both worlds.
WHAT’S IN THIS REVIEW?
| Cookie | Duration | Description |
|---|---|---|
| __cfduid | 1 month | The cookie is used by cdn services like CloudFlare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| cookielawinfo-checkbox-advertisement | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Advertisement". |
| cookielawinfo-checkbox-analytics | 1 year | This cookies is set by GDPR Cookie Consent WordPress Plugin. The cookie is used to remember the user consent for the cookies under the category "Analytics". |
| cookielawinfo-checkbox-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-non-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Non-necessary". |
| cookielawinfo-checkbox-performance | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 1 year | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-functional | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-others | 1 year | No description |