January 4, 2022
5 Cybersecurity Myths Debunked in 2025
When you think about it, myths are just a real-life version of the telephone game… A person hears [...]
WHAT’S IN THIS REVIEW?
Disclaimer: Partnerships & affiliate links help us create better content. Learn how.
As technology becomes more sophisticated, cyber attacks are trailing closely behind. That’s why it’s crucial to take the necessary steps to #BeCyberSmart and protect yourself against online threats. The month of October is Cybersecurity Awareness Month, and it’s a reminder to stay one step ahead of cyber criminals. There’s no single, foolproof tactic to keep your online data private and secure. So, we compiled a list of simple tips to give you control and significantly reduce your chances of falling victim to a cyber attack.

Did you know 66% of Americans use the same password across multiple accounts? To be fair, this is completely understandable. Trying to remember a unique password for every account is nearly impossible. But, that certainly doesn’t mean you should be using the same password for all your accounts. I say this because human error is the #1 factor of all cyber breaches—and this includes using weak passwords.
Your passwords are the first line of defense to protect your online accounts, so make sure you know how to create a strong password. Don’t use common passwords like 123456, password, or 111111. These are a hacker’s dream come true and will exponentially increase your chances of falling victim to a cyber breach.
According to a study by NordPass, the average person has about 100 passwords to remember. Think about it, we have passwords for numerous online accounts to pay bills, check our emails, shop online, stream TV shows and movies, book appointments, request transportation, order food—the list goes on! So, if you want to eliminate your frustration of trying to remember all your passwords, use a password manager service. Password managers use high-grade encryption protocols to keep all your passwords safe. The best part, you only have to remember one master password to access the rest.
Pro Tip: Many password managers can generate strong, unique passwords for you, so you don’t have to worry about creating them yourself.
Want to sign up for one now? Check out the 5 best password managers on the market today!
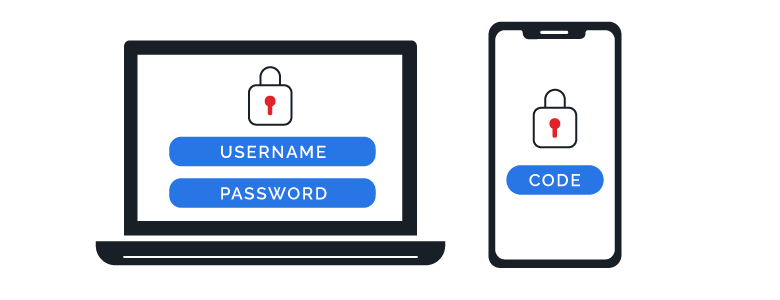
Multi-factor or two-factor authentication is another powerful tactic to implement for strong cybersecurity. By connecting a trusted device to your accounts, you can enable an authentication layer—such as fingerprint verification or entering a unique code sent to your device. This will keep cyber criminals from breaching your accounts even if they guess your password correctly.

Typically, phishing scams come in the form of an email or text message and appear to come from popular companies or someone you know. If you receive an unsolicited message, do not comply with their instructions, download any attachments, or click suspicious links. It’s most likely a cyber criminal attempting to deploy malicious software or steal sensitive information.
Ignoring software updates can be a tough habit to break. But, you could be doing yourself a disservice and increasing your chances of a cyber attack. Implementing software updates on your devices, browsers, and apps will ensure you have the most secure version available. When you ignore these updates, hackers can target you and take advantage of your outdated software containing security flaws. So, don’t wait, update!

Malware or other cyber threats can steal critical files or seriously damage your system. By performing regular backups to a separate storage drive, you’ll have the means to restore your files to their previous state. Yes, it’s an extra step—but, it provides a safety net when your system has been compromised.
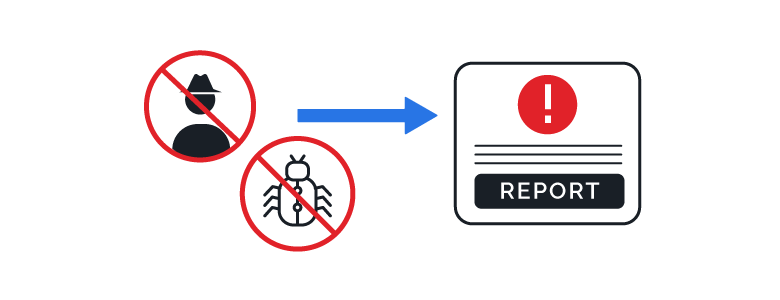
If you encounter a cybersecurity threat, there’s a high chance you’re one of many being targeted by a hacker. Report these incidents so authorities can investigate and take proper action to eliminate these threats. You can file an incident report to the FBI, your FBI Field Office, the Federal Government, or the Cybersecurity & Infrastructure Security Agency (CISA).
This is especially relevant when you’re connecting to public WiFi networks. While it does offer convenience, many cyber criminals target users on these networks because they’re transferring unsecured and unencrypted data. Installing a virtual private network (VPN) to your device will ensure your IP address and online activity is encrypted, private, and secure.
Transferring data online has evolved to an effortless stage. It’s an undeniable luxury but comes with risks we simply can’t ignore. Cyber criminals are out there hunting for opportunities to access your data and use it for personal gain. These 7 tips will not only decrease your chances of a cyber attack, but also help build a digital environment that is safer for everyone.
| Cookie | Duration | Description |
|---|---|---|
| __cfduid | 1 month | The cookie is used by cdn services like CloudFlare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| cookielawinfo-checkbox-advertisement | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Advertisement". |
| cookielawinfo-checkbox-analytics | 1 year | This cookies is set by GDPR Cookie Consent WordPress Plugin. The cookie is used to remember the user consent for the cookies under the category "Analytics". |
| cookielawinfo-checkbox-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-non-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Non-necessary". |
| cookielawinfo-checkbox-performance | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 1 year | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-functional | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-others | 1 year | No description |