January 4, 2022
5 Cybersecurity Myths Debunked in 2025
When you think about it, myths are just a real-life version of the telephone game… A person hears [...]

WHAT’S IN THIS REVIEW?
Disclaimer: Partnerships & affiliate links help us create better content. Learn how.
Internet of Things (IoT) specialist Ubiquiti was the target of a network breach in January 2021, after they received a ransom note which demanded 50 Bitcoin in exchange for stolen proprietary data. It equated to a $2 million amount, while a VPN (Surfshark) had a large role to play as the story developed.
Here’s everything you need to know about the 2021 Ubiquiti networks breach, and why there are lessons to be learned for the average VPN user.
As it turns out, the ransom note originated from a former member of staff, who still had access to important data via an AWS account.
Nickolas Sharp, a senior developer at Ubiquiti, was charged after his real IP address was allegedly exposed due to the combination of a poor internet connection and the fact that he forgot to turn on the kill switch while using Surfshark VPN.
“Ubiquiti refused to pay and instead called law enforcement, which eventually identified Sharp as the hacker after linking the attacker’s VPN connection to a Surfshark account purchased with Sharp’s PayPal account. In addition, the VPN connection also failed during the intrusion, temporarily exposing the attacker’s real IP address, which authorities also linked to Sharp.”
It came to light after the company told customers to change their passwords, even if there was “no indication that there has been unauthorized activity with respect to any user’s account.”
Meanwhile, the FBI raided Sharp’s house in March 2021, after which he allegedly posed as a whistleblower and reached out to various news outlets to plant stories about Ubiquiti’s hack and its aftermath. Their stock price went down 20% as a result.
The Internet of Things (IoT) giant released a statement in which they discussed the ‘cybersecurity incident’, confirming much of the story.
“As we informed you on January 11, we were the victim of a cybersecurity incident that involved unauthorized access to our IT systems. Given the reporting by Brian Krebs, there is newfound interest and attention in this matter, and we would like to provide our community with more information.”
“At the outset, please note that nothing has changed with respect to our analysis of customer data and the security of our products since our notification on January 11. In response to this incident, we leveraged external incident response experts to conduct a thorough investigation to ensure the attacker was locked out of our systems.”
“These experts identified no evidence that customer information was accessed, or even targeted. The attacker, who unsuccessfully attempted to extort the company by threatening to release stolen source code and specific IT credentials, never claimed to have accessed any customer information. This, along with other evidence, is why we believe that customer data was not the target of, or otherwise accessed in connection with, the incident.”
“At this point, we have well-developed evidence that the perpetrator is an individual with intricate knowledge of our cloud infrastructure. As we are cooperating with law enforcement in an ongoing investigation, we cannot comment further.”
“All this said, as a precaution, we still encourage you to change your password if you have not already done so, including on any website where you use the same user ID or password. We also encourage you to enable two-factor authentication on your Ubiquiti accounts if you have not already done so.”
But what does this have to do with the average VPN user interested in looking after their privacy?
Surfshark had a major role to play, with Sharp going so far as to claim “that someone else might have used his personal PayPal account to pay for the Surfshark VPN used in the attack.” This is a fairly unlikely scenario, although there’s no way to say for sure.
What we do know is that Surfshark is based in the Netherlands where “police can’t track live, encrypted VPN traffic, but if they have a court order, they can go to your ISP (Internet Service Provider) and request connection or usage logs. Since your ISP knows you’re using a VPN, they can direct the police to them. Whether you VPN provider gives up that information depends on factors such as the jurisdiction and the VPN’s privacy policy.”
That’s a fair assessment, but what does the Surfshark Privacy Policy actually say? According to their website:
“We only disclose personal information to law enforcement authorities or courts of competent jurisdiction when we are asked and legally obliged to do so,” while they point to a warrant canary as proof that they’ve handed over no data.
It’s worrying that the connection dropped and exposed Sharp’s IP, although that could have been solved with the use of the VPN kill switch.
Meanwhile, the linking of a PayPal account with a VPN service is a common method to identify users. (It’s why we’d always advocate for anonymous payment methods, such as cryptocurrencies or even gift cards.)
Sharp also had the opportunity to do so and chose otherwise, as our SurfShark review notes:
“Surfshark also accepts multiple cryptocurrency payments, so even Surfshark won’t know who you are upon signing up. It requires an email address to create an account, but does not make you verify it – which means you can use a dummy account if need be.”
Get an automatic kill switch to protect your internet connection with Surfshark.
In other words, it’s not especially difficult to use Surfshark anonymously, and you should always be wary of the connection dropping unexpectedly.
If there’s one lesson to take away from the Ubiquiti breach, it should be the importance of using a kill switch at all times. (This is especially important if you suffer from inconsistent connection speeds, as seen in the story above.)
In case you weren’t aware, a kill switch automatically disconnects your device from the internet if the VPN drops out unexpectedly. This stops your real IP address from being exposed to any platform or service. It’s also ideal if you’d prefer to keep clear of trackers, hackers, or anyone interested in your personal data.
Surfshark even makes sure that their Kill Switch is easy to find, with a toggle option found on the right-hand side of the main app page. You can also navigate into the VPN settings menu to find an additional Kill Switch option.
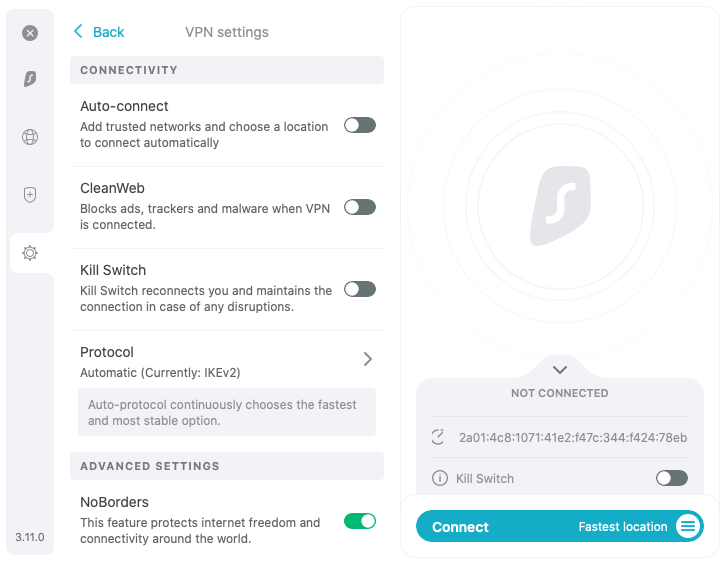
However, as you’ll see from the screenshot above, it’s not set to be on via the default settings.
If you’re using a VPN for privacy rather than entertainment, make sure that the app has kill switch functionality and that it’s on at all times.
Ignoring the criminal element of the story for one moment, the Ubiquiti data breach highlights why it pays to understand how a VPN works before using one for anything that you would consider to be important.
This can include anything from online communications in a restricted country, to keeping the data the likes of Google collect about you to a minimum. The same goes for paying

| Cookie | Duration | Description |
|---|---|---|
| __cfduid | 1 month | The cookie is used by cdn services like CloudFlare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| cookielawinfo-checkbox-advertisement | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Advertisement". |
| cookielawinfo-checkbox-analytics | 1 year | This cookies is set by GDPR Cookie Consent WordPress Plugin. The cookie is used to remember the user consent for the cookies under the category "Analytics". |
| cookielawinfo-checkbox-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-non-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Non-necessary". |
| cookielawinfo-checkbox-performance | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 1 year | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-functional | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-others | 1 year | No description |